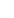In order to prevent accidents from occurring, we provide information security diagnosis services by experts that can be carried out during normal times.
Web application diagnostics
Service features
At FRONTEO, diagnostic engineers with specialized knowledge identify potential security problems with your website and provide advice on necessary countermeasures.
Service Overview
We conduct inspections via the Internet using our own testing tools while ensuring standardization of quality and comprehensiveness of diagnostic items.
Because specialized diagnostic engineers conduct manual inspections while taking into account the structure of the application, it is possible to detect vulnerabilities that are difficult to detect with traditional diagnostic tools.
In addition, we do not simply investigate the existence of vulnerabilities, but also verify the specific impact that vulnerability has on the customer's system.The report is created in an easy-to-understand manner, including a 5-level evaluation by engineers, an overall review, explanations of vulnerabilities and risks (degree of impact), and countermeasures, and incorporates screen captures.
Web application diagnosis overview
| Inspection item | Description | Typical vulnerabilities |
|---|---|---|
| Items related to user authentication | We check whether unauthorized application usage is possible by using unauthorized services or impersonating others. Also, check whether encrypted communication is available and whether the server certificate settings are appropriate. |
|
| Items related to content access approval | We check to see if there is a possibility of impersonation of authorized users and leakage of personal information due to flaws in session management used to maintain information for each user. |
|
| Items related to attacks against clients | By attacking the user's browser, it checks whether it is possible to execute arbitrary scripts or spoof content. |
|
| Items related to command execution | We investigate the behavior of programs when character strings, etc. that are not used in normal use are entered, and check for abnormal service stoppages or the possibility of leaks of important information due to unauthorized manipulation of the OS or database. |
|
| Items related to information acquisition | Check whether there are default pages or sample pages attached to the web server or web application. Also, check for the possibility of unexpected information being exposed by exploring files that are not publicly available. |
|
| Items related to misuse of application features | We check for structural and functional weaknesses in web applications and verify the possibility of various attacks. |
|
Penetration diagnosis
Service features
At FRONTEO, we objectively evaluate the attack resistance and security level by performing pseudo-attacks on customer systems (servers, network equipment) that are equivalent to those of an attacker.Provide system enhancement measures.
Service Overview
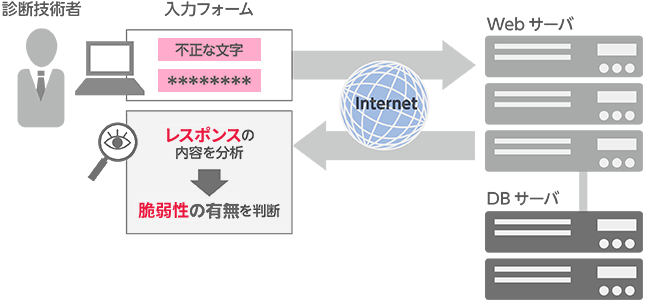
We use multiple tools and manual methods to verify the presence or absence of vulnerabilities in target servers, network devices, etc. via the Internet and from internal LAN segments that you specify.
Furthermore, we will verify whether the attack is possible using a program that uses known vulnerabilities published on the Internet to infiltrate servers, or our own scripts.
Penetration test
Differences between penetration diagnosis and vulnerability scanner testing
Vulnerability scanners only perform tests using software.It is possible to conduct inspections at low cost and in a short period of time.However, since vulnerability analysis is performed based on information that can be obtained via the network, there are some vulnerabilities that cannot be discovered.We recommend testing using a vulnerability scanner to customers who have never performed testing before, and to customers who want to efficiently understand the security level of their systems at a low cost.
Penetration testing involves manual inspection by an inspector in addition to inspection by a vulnerability scanner.Because it examines complex issues that cannot be detected by vulnerability scanners, it is possible to understand the vulnerabilities that exist in the system in accordance with the current security risks.Penetration testing is recommended for customers seeking a high level of security.
Security consulting
Features of security consulting
FRONTEO conducts on-site current situation analysis and information system platform diagnosis by experts with extensive consulting experience.After assessing your information security environment, we will help you formulate a response policy.
We also offer solutions tailored to the customer's security environment and provide support for selection and implementation.
Service Overview
Using FRONTEO platform diagnosis, we investigate the existence of vulnerabilities in the customer's target system and evaluate the technical security level.
In addition, we conduct on-site analysis of the current situation from various security perspectives, including physical security such as access control and lock management, operational rule development, and human security such as employee/contractor training. .
We objectively evaluate the current level of information security and IT controls by comparing the results of platform diagnosis and on-site current situation analysis with the requirements required by internationally reliable security standards such as ISMS and PCI DSS. .
We also support the formulation of policies to strengthen systems tailored to the customer's actual circumstances, including the development of security regulations and the introduction of solutions as necessary.
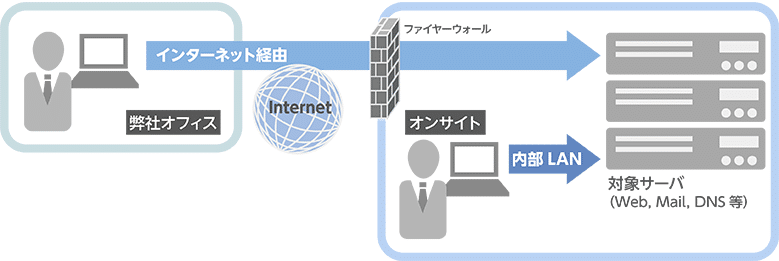
1. Conducting an interview survey
2. Conducting a field survey
3. Carrying out technical verification of the system
4. Security requirements organization
5.Implementation of analysis results report
6. Presentation of improvement plans and strengthening measures
Service provision flow
We analyze and evaluate the current state of information security through interviews and field surveys.
If necessary, we will present measures to strengthen your organization's security posture.
FRONTEO's Legal Tech AI
Please feel free to consult us.